Trezor Hardware Wallet: Take Full Control of Your Crypto Safely
In the digital age, holding your own keys is the new financial freedom. With cyber threats, centralized exchange hacks, and phishing scams on the rise, relying on third-party platforms to store your digital assets is no longer a safe bet. Enter the Trezor Hardware Wallet—a secure, offline storage solution that gives you complete control over your cryptocurrency.
Whether you're safeguarding Bitcoin, Ethereum, or altcoins, Trezor’s hardware wallets are trusted by millions globally to keep private keys offline and under the owner’s protection.
🧠 Why Choose a Hardware Wallet Like Trezor?
Unlike hot wallets, which are always connected to the internet, hardware wallets keep your private keys in a physical, offline device. This eliminates exposure to most common threats like keyloggers, malware, and phishing attacks.
The Trezor Hardware Wallet is more than just a USB stick—it’s a cryptographic vault. Built by SatoshiLabs, the creators of the world’s first hardware wallet, Trezor has become a gold standard for digital asset security.
Why Trezor stands out:
- Proven track record since 2014
- Open-source firmware and transparent development
- Secure chip design without closed-source "black boxes"
- Regular firmware updates and global community support
📦 Trezor Model One vs. Model T: What’s the Difference?
Trezor offers two hardware wallet models designed for different needs:
Trezor Model One
- The most affordable and compact option
- Basic display with two-button navigation
- Supports 1,000+ coins and tokens, including BTC and ETH
Trezor Model T
- Advanced model with a full-color touchscreen
- Enhanced support for coins like XRP, ADA, XMR
- Features Shamir Backup, microSD encryption, and more
- Ideal for users with larger or diverse portfolios
Both models offer the same core security, so your choice depends on usability preferences and the range of assets you need to manage.
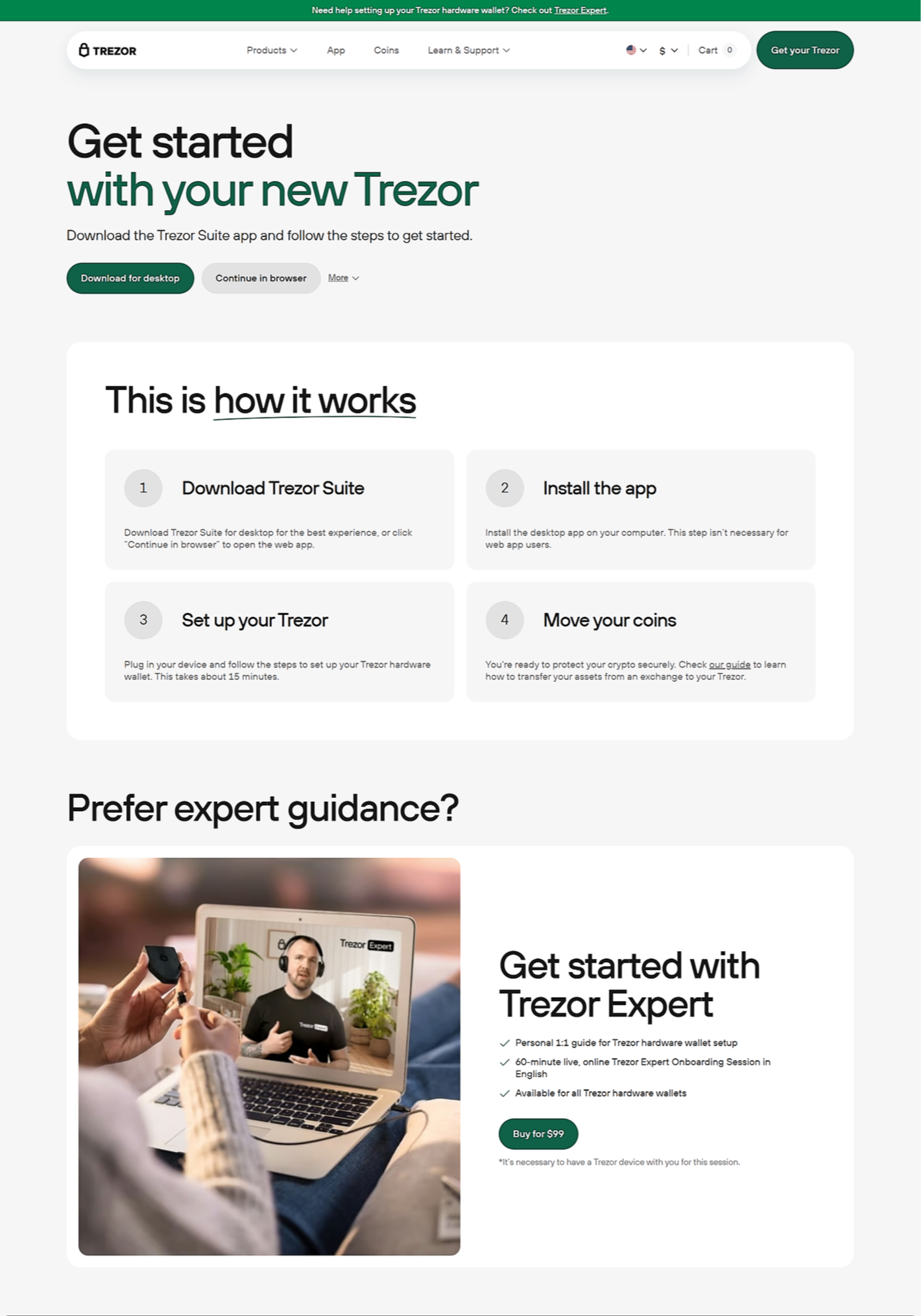
🚀 How to Set Up Trezor the Safe and Proper Way
To set up your Trezor securely, always begin at the official portal: Trezor.io/start. This guarantees you avoid counterfeit firmware and phishing traps.
Steps to follow:
- Visit Trezor.io/start
- Select your device (Model One or Model T)
- Download and install Trezor Suite, the official management interface
- Connect your Trezor device via USB
- Install the latest firmware
- Create a new wallet and generate your recovery seed
- Write down the 12–24 word recovery phrase securely
- Set a unique PIN code
- Start sending, receiving, and managing crypto securely
Every action—from device setup to transaction approval—must be physically confirmed on your Trezor, adding an extra layer of safety.
🔐 Seed Backup: Your Lifeline in Emergencies
When you generate your Trezor wallet, you’ll receive a recovery seed phrase. This phrase allows you to recover your wallet on any Trezor device, should your original one get lost, stolen, or damaged.
Best practices for seed protection:
- Never store it digitally (no screenshots or cloud notes)
- Write it on the provided card or, better, use a metal backup
- Store it in a secure, fireproof, waterproof location
- Never share it with anyone—not even Trezor support
Advanced users can enable passphrase protection or Shamir Backup for added control and recovery flexibility.
🧰 Trezor Suite: Your Control Panel for Digital Assets
Trezor Suite is the desktop app that helps you manage your assets securely. It integrates seamlessly with your hardware wallet and ensures no private data ever leaves the device.
Features of Trezor Suite:
- Manage BTC, ETH, ERC-20 tokens, and more
- Check balances, send/receive funds, and label accounts
- Use built-in coin swaps via integrated exchanges
- Privacy options like Tor support
- Track portfolio value in real time
Plus, Trezor Suite also works with MetaMask, enabling secure DeFi access while keeping your private keys offline.
⚙️ Advanced Security Tools for Pro Users
If you’re an experienced crypto user or storing large amounts, Trezor offers powerful security tools:
- Passphrase Encryption: Adds a custom password layer on top of the recovery phrase
- Hidden Wallets: Use different passphrases to access multiple wallets
- Multisig Support: Collaborate on secure accounts requiring multiple approvals
- Shamir Backup: Split your seed into multiple shares for disaster-proof recovery
These tools put maximum control in your hands, with no third-party access ever.
🌐 Compatibility With Wallets and Web3 Apps
Trezor integrates smoothly with major wallets and Web3 platforms. You can use it with:
- MetaMask for Ethereum and NFTs
- MyEtherWallet (MEW) for ERC-20 token management
- Electrum for advanced Bitcoin transactions
- Exodus for a sleek interface and multi-asset support
Trezor ensures your private keys remain offline and inaccessible even during Web3 interactions.
✅ Final Thoughts: Why Trezor Is the Smartest Crypto Investment
In the volatile and often risky world of cryptocurrencies, your best protection is ownership and control—and Trezor gives you exactly that.
With unmatched security, regular updates, and total transparency, Trezor is not just a device—it’s your personal fortress for digital wealth.
🔐 Get started the right way at Trezor.io/start and take control of your crypto future today.
Trezor Hardware Wallet: Take Full Control of Your Crypto Safely
In the digital age, holding your own keys is the new financial freedom. With cyber threats, centralized exchange hacks, and phishing scams on the rise, relying on third-party platforms to store your digital assets is no longer a safe bet. Enter the Trezor Hardware Wallet—a secure, offline storage solution that gives you complete control over your cryptocurrency.
Whether you're safeguarding Bitcoin, Ethereum, or altcoins, Trezor’s hardware wallets are trusted by millions globally to keep private keys offline and under the owner’s protection.
🧠 Why Choose a Hardware Wallet Like Trezor?
Unlike hot wallets, which are always connected to the internet, hardware wallets keep your private keys in a physical, offline device. This eliminates exposure to most common threats like keyloggers, malware, and phishing attacks.
The Trezor Hardware Wallet is more than just a USB stick—it’s a cryptographic vault. Built by SatoshiLabs, the creators of the world’s first hardware wallet, Trezor has become a gold standard for digital asset security.
Why Trezor stands out:
- Proven track record since 2014
- Open-source firmware and transparent development
- Secure chip design without closed-source "black boxes"
- Regular firmware updates and global community support
📦 Trezor Model One vs. Model T: What’s the Difference?
Trezor offers two hardware wallet models designed for different needs:
Trezor Model One
- The most affordable and compact option
- Basic display with two-button navigation
- Supports 1,000+ coins and tokens, including BTC and ETH
Trezor Model T
- Advanced model with a full-color touchscreen
- Enhanced support for coins like XRP, ADA, XMR
- Features Shamir Backup, microSD encryption, and more
- Ideal for users with larger or diverse portfolios
Both models offer the same core security, so your choice depends on usability preferences and the range of assets you need to manage.
🚀 How to Set Up Trezor the Safe and Proper Way
To set up your Trezor securely, always begin at the official portal: Trezor.io/start. This guarantees you avoid counterfeit firmware and phishing traps.
Steps to follow:
- Visit Trezor.io/start
- Select your device (Model One or Model T)
- Download and install Trezor Suite, the official management interface
- Connect your Trezor device via USB
- Install the latest firmware
- Create a new wallet and generate your recovery seed
- Write down the 12–24 word recovery phrase securely
- Set a unique PIN code
- Start sending, receiving, and managing crypto securely
Every action—from device setup to transaction approval—must be physically confirmed on your Trezor, adding an extra layer of safety.
🔐 Seed Backup: Your Lifeline in Emergencies
When you generate your Trezor wallet, you’ll receive a recovery seed phrase. This phrase allows you to recover your wallet on any Trezor device, should your original one get lost, stolen, or damaged.
Best practices for seed protection:
- Never store it digitally (no screenshots or cloud notes)
- Write it on the provided card or, better, use a metal backup
- Store it in a secure, fireproof, waterproof location
- Never share it with anyone—not even Trezor support
Advanced users can enable passphrase protection or Shamir Backup for added control and recovery flexibility.
🧰 Trezor Suite: Your Control Panel for Digital Assets
Trezor Suite is the desktop app that helps you manage your assets securely. It integrates seamlessly with your hardware wallet and ensures no private data ever leaves the device.
Features of Trezor Suite:
- Manage BTC, ETH, ERC-20 tokens, and more
- Check balances, send/receive funds, and label accounts
- Use built-in coin swaps via integrated exchanges
- Privacy options like Tor support
- Track portfolio value in real time
Plus, Trezor Suite also works with MetaMask, enabling secure DeFi access while keeping your private keys offline.
⚙️ Advanced Security Tools for Pro Users
If you’re an experienced crypto user or storing large amounts, Trezor offers powerful security tools:
- Passphrase Encryption: Adds a custom password layer on top of the recovery phrase
- Hidden Wallets: Use different passphrases to access multiple wallets
- Multisig Support: Collaborate on secure accounts requiring multiple approvals
- Shamir Backup: Split your seed into multiple shares for disaster-proof recovery
These tools put maximum control in your hands, with no third-party access ever.
🌐 Compatibility With Wallets and Web3 Apps
Trezor integrates smoothly with major wallets and Web3 platforms. You can use it with:
- MetaMask for Ethereum and NFTs
- MyEtherWallet (MEW) for ERC-20 token management
- Electrum for advanced Bitcoin transactions
- Exodus for a sleek interface and multi-asset support
Trezor ensures your private keys remain offline and inaccessible even during Web3 interactions.
✅ Final Thoughts: Why Trezor Is the Smartest Crypto Investment
In the volatile and often risky world of cryptocurrencies, your best protection is ownership and control—and Trezor gives you exactly that.
With unmatched security, regular updates, and total transparency, Trezor is not just a device—it’s your personal fortress for digital wealth.
🔐 Get started the right way at Trezor.io/start and take control of your crypto future today.
Made in Typedream